Application Security
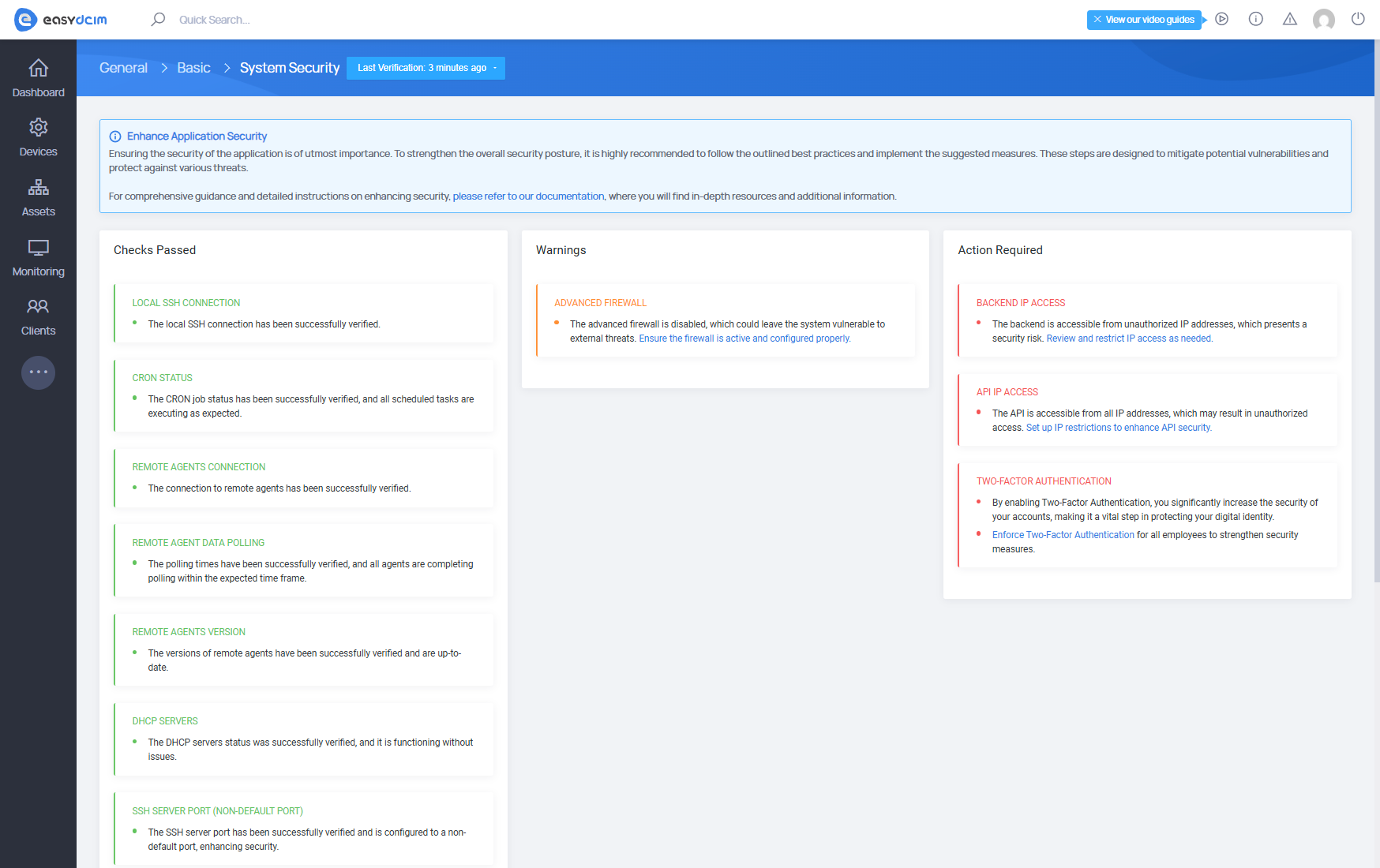
System Security Checks
EasyDCIM performs a series of automatic background tests every five minutes to verify the system’s most critical settings. You can also run these tests manually whenever needed—for example, after updates or configuration changes.
Key checks include:
- Local SSH Connection – Verifies local SSH availability. Use
php /opt/easydcim/artisan ssh:generateif needed. - Free Disk Space – Checks available disk space on the EasyDCIM server. If free space falls below the configured threshold (currently 10 GB), the system marks this as a critical issue and notifies the administrator.
- SSH Server Port – Warns if SSH uses the default port 22. Configure a custom port and update it in settings.
- CRON Status – Ensures required scheduled task entries exist in
/etc/crontab. - Remote Agents Connection – Validates communication between EasyDCIM and remote agents.
- DHCP Servers – Monitors the operational status of DHCP on remote agents.
- Remote Agent Data Polling – Confirms polling completes within 300 seconds; otherwise, consider resource upgrades.
- Backend & API IP Access – Recommends IP whitelisting to restrict unauthorized backend/API access.
- Advanced Firewall (ModSecurity) – Advises enabling and configuring ModSecurity with proper IP whitelist settings.
- Redis Status – Verifies that Redis server is running.
- SSL Configuration – Recommends SSL if the system is exposed via a public domain.
- PHP, Debian, and EasyDCIM Versions – Confirms compatibility by requiring PHP 8.3.X and Debian 12.X.
- Remote Agents Version – Suggests updating agents to the latest version.
- Two-Factor Authentication – Verifies if 2FA is enabled for backend access.
Firewall Rules
EasyDCIM and remote agents rely on various ports for secure communication. You can limit access to only necessary ports using a firewall such as iptables.
EasyDCIM uses:
22/TCP– for SSH (custom port possible)80/TCP– for HTTP443/TCP– for HTTPS6081–6200/TCP– for noVNC console (Websockify sessions)
Client Area uses:
8444/TCPand8443/TCP– for local installations running on the same server as EasyDCIM80/TCPand443/TCP– for external installations running on a separate domain or IP address6081–6200/TCP– for proxied noVNC (Websockify) console sessions between the Client Area and EasyDCIM backend
Remote Agents use:
8080/TCP,8081/TCP– for HTTP/HTTPS22/TCP– for local SSH67/UDP,68/UDP,69/UDP– for DHCP/TFTP139/TCP,445/TCP– for Samba5901–6000/TCP– for Docker-based console access
Outgoing Connections:
- Servers:
623/TCP,623/UDP,443/TCP,80/TCP - Network Devices:
161/UDP,162/UDP,22/TCP,830/TCP
License Server:
Connection to license.easydcim.com (5.161.211.169) over 443/TCP is required.
Additional Security Measures
EasyDCIM offers several built-in features to strengthen system access control and protect both the backend and API layers.
Two-Factor Authentication
Add an extra layer of security for backend logins. Learn more in the Two-Factor Authentication guide.
Allowed IP Addresses
Limit backend and API access by defining allowed IPv4/IPv6 addresses or subnets in CIDR format. You can configure these restrictions under the System Access tab in global settings.
Examples:
- Backend IPs:
192.168.56.1,192.168.56.0/24
Additional API-specific security fields available in system configuration:
- Allowed IP Addresses (Admin API): Specify the list of IPv4/IPv6 addresses that will be included in the whitelist. Applies to the Admin API section.
- Allowed IP Addresses (Client API): Specify the list of IPv4/IPv6 addresses that will be included in the whitelist. Applies to the Client API section.
Client Area Access
Within Settings → Basic → Client Area, you can configure all backend parameters related to the Client Area connection, communication, and behavior.
For the full description of available backend options, see: Backend Configuration Fields



















